Securing the Industrial Internet
Designers realize that for the Industrial Internet security cannot be an afterthought. The bad news however is that they are reverting to the same security solutions that failed in the past and continue to fail as we write.
McKinsey and co estimate that the cost of ineffective cybersecurity will rise to three trillion dollars by 2020. Given the prediction that the Industrial Internet will have five to ten times the impact on society as the Internet itself there is an urgent need to rethink security for machines.
Learning from PKI History
Browse vendor marketing materials and it will feel like the 1990s never happened. It’s all key management, digital certificates and certificate authority hierarchies for 50 billion machines.
Doesn’t anyone remember the Years of PKI? Insanity is often defined as doing the same thing over and over again and expecting a different result. So has there been a wave of collective insanity that would make people believe it can work this time?
The answer is no, there simply hasn’t been an alternative. If all you have is a key then everything looks like lock. Like helicopter ejection seats, using PKI for the Industrial Internet is a bad idea that simply won’t go away.
Here are six reasons why:
1. It’s not a about data in motion. It’s about data at rest.
Bruce Schneier pointed out in 2006 that throughout the 1990s everyone was focused on data in motion when they should have been focused on data at rest.
This focus on communication between separate parties is also the reason modern security continues to fail.
It is like securing your home by digging a tunnel to your neighbor’s house. What matters for machines (and for your home) is protecting what’s inside it – ensuring that the software operating inside the device has not been compromised.
If the device is compromised then securing the communication from it won’t matter a fig.
2. It’s not about Confidentiality. It’s about Integrity.
Let’s look at possible integrity and confidentiality breaches for familiar devices. You choose.
|
|
Integrity Breach |
Confidentiality Breach |
|
Your Car |
Your braking system stops working. |
Your braking patterns are exposed. |
|
Your Flight |
Your plane’s instruments report that you are 1,000 feet lower than you actually are |
Your flight plan is posted on the Internet. (note: it already is) |
|
Your Local Power Station |
Critical systems compromised leading to shutdown or catastrophic failure |
Your electricity bill is published online. |
|
Your Pacemaker |
Shutdown and death |
Your heatbeat becomes public knowledge. |
|
Your Home |
Your security system is remotely disabled |
The contents of your fridge are “leaked”. You drink how much beer? |
3. Data Integrity is the Biggest Military Threat
Don’t take our word for it:
“The most serious national security threat looming in cyberspace may be the potential for vital data to be altered by cybermarauders, according to a cyber expert with the Office of the Director of National Intelligence (ODNI).
Speaking to an attentive audience at the AFCEA Global Intelligence Forum in the National Press Club in Washington, D.C., Sean Kanuck, national intelligence officer for cyber issues at the National Intelligence Council in the ODNI, admitted that the threat to data integrity keeps him awake at night.”
- Robert K. Ackerman, SIGNAL Online, July 31, 2013
“The nation’s top military officer said the United States lacks a strategy for cybersecurity, and data integrity remains one of the biggest security concerns for the Defense Department.
Speaking today at a conference on disruptive military technologies, sponsored by the Atlantic Council, Joint Chiefs Chairman Gen. Martin Dempsey warned the nation remains unprepared for a major cyber-attack.
– Dan Verton, Fedscoop, May 14, 2014“
Let’s face it if you want to take out a country you don’t need to steal secrets. You simply need to manipulate the software inside their power-grid, communications and transport systems and it’s game-over.
These are integrity attacks, and the reality is, that basing the integrity of networks and systems on the security of key-stores and the administrators who manage them, is a failed strategy.
4. Machines are different from humans!
PKI was designed for Alice and Bob to share secret messages not for massive scale continuous verification of the integrity of machines and the data they produce.
Communication is stateless – meaning that if Alice thinks her key has been compromised she can simply generate a new key pair, register the public key and previous communications (those before the key compromise) will not be impacted.
Machines however are stateful, meaning that the keys that are used to verify their integrity have to be secured and managed for the life of the machines and the data they produce.
This complexity is a recipe for disaster and at best will lead to a false sense of security. To quote Schneier “And therein lies the problem. Keys can no longer be stored in people’s brains. They need to be stored on the same computer, or at least the network, that the data resides on. And that is much riskier.”
5. Data starts off and finishes as data in rest.
In the human world Alice is only concerned about the communicaiton of her message to Bob. In the machine world however there is a myriad of interacting devices, customer transactions, user activities, access, authentication and ‘handoff’ automation, virtualization and application launches, software deliveries, data from API interactions and their associated messages, as well as sensor data from remote devices.
By focusing only on communication there is no chain of custody or way to audit the lifetime of the data from sensor fusion, ingest and analytics across data lakes hosted in different environments administered by different organizations. One compromise anywhere in the chain and the reliability of the data being collected and any conclusions derived thereof will be suspect.
In the machine world data starts off and finishes as data at rest and we need to think about the entire lifetime of the data, not just securely communicating between devices.
6. There will always be vulnerabilities
The underlying assumption today is that machines and the sensor data being managed by machines can be secured. This is a false premise. Machines, their communications protocols, their software, rules, and their exposed APIs will always have flaws.
The Industrial Internet and the sensors that feed it MUST ASSUME COMPROMISE!
If perimeter security defense systems and confidential encryption tunnels are ultimately compromised, how then can the Industrial Internet and the data lakes it feeds be secured and assured to have integrity? – and in fact trusted in a way that ensures the decisions machines are making to tweak and optimize performance is coming from trusted sources and utilizing the right algorithms and rules engines?
Consider for a moment four years ago when ‘Stuxnet’ was the cyber-attack du-jour responsible for taking down the Iranian Natanz facility. If we are to believe press reports, Stuxnet was the result of a joint US-Israeli collaboration to delay Iran’s nuclear program. This facility was NOT connected to the Internet – and to date, how Natanz was infected with Stuxnet remains a mystery. However, the lesson for the Industrial Internet is that if a nation-state can take down an air gapped nuclear control facility via a cyber exploit with disastrous consequences, how much easier is this attack if assets like nuclear facilities, aircraft, vehicles, or your health sensors are in fact connected to the Internet. Cyber liability insurance hasn’t even begun to address nor cover these glaring liabilities and potential for loss of life or property.
Conclusion
When Whit Diffie proposed public key cryptography in 1976 he wasn’t thinking about integrity – he was thinking about two parties exchanging keys across an insecure channel.
Integrity (of the messages) was a secondary application and although PKI based digital signatures can be used for integrity of data at rest the complexity and cost of key management make it impossible to implement at scale.
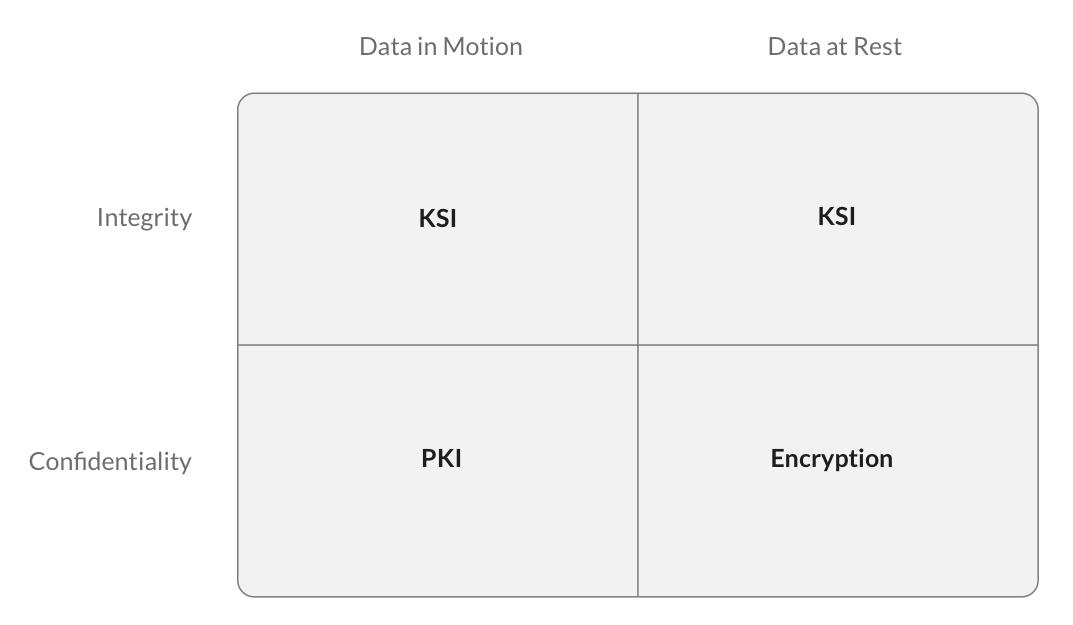
Figure: The best of all worlds
Ultimately both PKI are KSI are tools optimized for particular tasks. PKI for ensuing confidentiality of data in motion via key exchange and, KSI for ensuring the integrity and authenticity of systems and data.
Oscar Wilde was correct. Enslaving machines will be critical to the future of our digital society. To enslave you have to secure and the time is long, long overdue for fundamental innovation to upgrade from a security technology that was invented almost 40 years ago to allow humans to communicate securely to one that solves the right problem for the Industrial Internet, an always connected, high volume decentralized world of machines whose system integrity is critical.